Tag: security
-
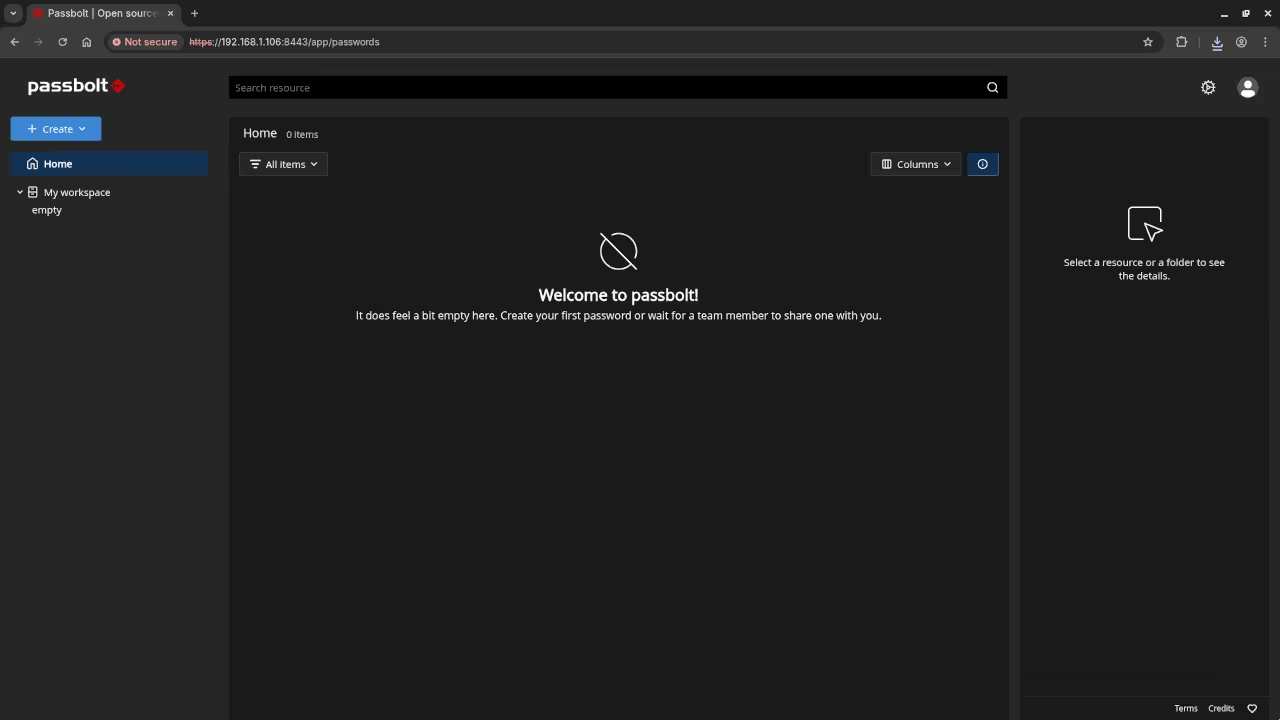
How to Self-Host Passbolt: An Open-Source Password Manager
How to Install Passbolt Community Edition on Your Server (Using Podman with Self-Signed SSL) Introduction In this guide, we will walk you through setting up Passbolt Community Edition using Podman and self-signed SSL certificates for HTTPS.
Written by
-
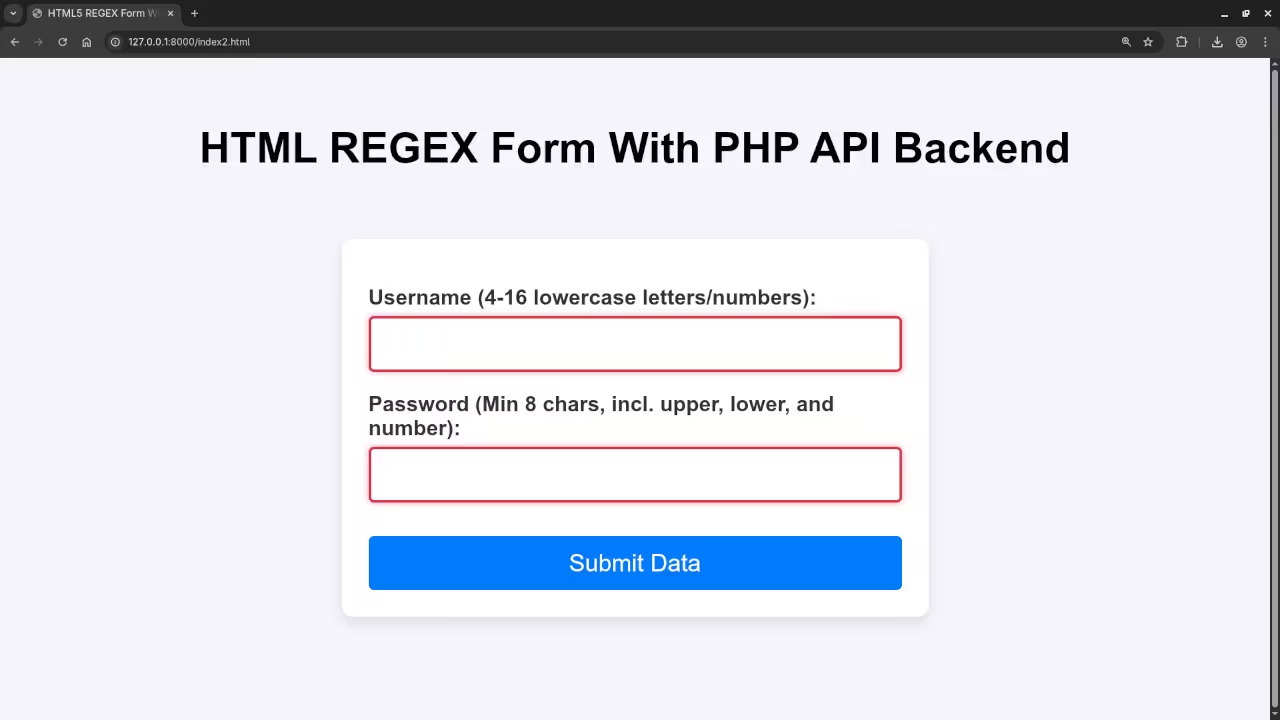
Server-side Defense: PHP Validation, Hashing, And MariaDB Storage
PHP Validation, Santization, and Storage Every developer knows the challenge: you need to collect user data via a form, and that data must be both valid and securely stored.
Written by
-
Install Froxlor With Wildcard SSL
How to Install Froxlor with Wildcard SSL Using Podman-Compose: A Simple Beginner’s Guide Introduction: In this guide, we’ll install Froxlor inside Podman containers using podman-compose for simplified management.
Written by

-
High Resolution Old Phone HTML5 Security Camera
Track An Area Using Higher Resolution Mobile Phone Camera An obsolete phone can be turned into a webcam using a custom application.
Written by

-
Node.js Websockets Chicken Security Camera
Monitor An Area Using Old Mobile Phone Camera An obsolete phone or portable device can be turned into a webcam using a custom application.
Written by

-
Choose And Style Phone HTML5 Security Camera
Track An Area Using Mobile Phone Camera An obsolete phone can be turned into a webcam using a custom application.
Written by

-
Old Phone HTML5 Security Camera SSL Via Stunnel
Track An Area Using Mobile Phone Camera An obsolete phone can be turned into a webcam using a custom application.
Written by
