How Two-Factor Authentication Works
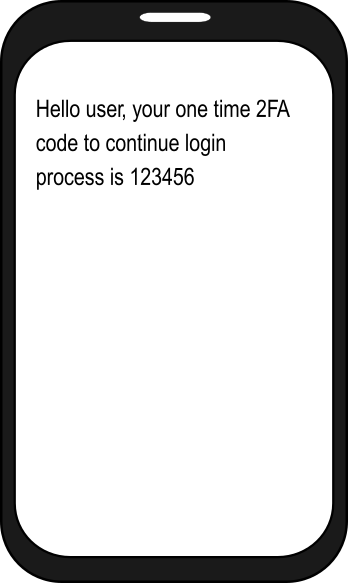
Two-Factor Authentication (2FA) works by sending alphanumeric characters to an email address or mobile phone. During the login process after entering correct username and password, the send code is expected to be input in order to complete the login process.
Email Two-Factor Authentication Issues:
- If your login credentials are compromised, the hacker will already have the email address which also commonly used as the username.
- Most platforms show or ask for the email address to be entered before sending the 2FA code. A hacker can then send phishing emails or spam emails to the email address.
- Email 2FA is not a secure method of communication because the messages are encrypted.
A better option would be to secure the platform by never sending passwords over email and never having third party scripts especially trackers on the login page.
Voice Call Two-Factor Authentication Issues:
- This method assumes that a user has a phone and wants to receive phone calls from unknown numbers.
- Relying on a phone call means a user needs to add their phone number to the platform which motivates a hacker to sell the phone number to scrupulous actors.
- The user will have to pay for unnecessary long distance charges.
- Voice Call 2FA is not a secure method of communication because the messages are encrypted. Also the phone voice call can be heard by other people nearby.
- Assumes that a user has full unfettered access to the phone or phone line, which might be on temporary loan or compromised such as an abusive relationship both at work and home.
- Assumes that a user will have reliable phone service. In Canada, telecommunications provider Rogers Communications had a major outage on 2022-07-08 affecting individuals and businesses.
A better option would be selecting a random question that only the user can answer. The online bank Tangerine has used the random question method since at least 2009.
Text Message Two-Factor Authentication Issues:
- Same issues as voice call 2FA in that it assumes a user has a phone with a text message plan.
- Means that a user is not allowed to travel as they will have to pay roaming charges.
- A compromised platform will allow hackers to have access to users phone numbers and send spam text messages.
- When the phone service is down or unavailable in remote rural areas, the user will not be able to login. Also the phone text message can be seen by other people nearby, especially with modern notifications.
- Spammers and scammers can mimic the simply text messages and redirect users to malicious sites.
A better option would be asking a suspicious question that only the user can answer. Tracking the location of a user is a privacy issue and does not improve security.
CAPTCHA Authentication Issues:
- One way to separate humans and bots is with the Turing test for machine intelligence. CAPTCHA tests typically use images, a check-box or simple math calculation. Modern versions implement a timer and click algorithm to verify that the user is a human.
- Users dislike CAPTCHA methods because they are repetitive and impersonal due to the random generated images. There is no need to keep showing CAPTCHA methods if a user just logged off.
- CAPTCHA will not work when a user disables JavaScript or a web browser is not compatible
- Web browser cache can prevent CAPTCHA from loading.
- CAPTCHA will not work when some countries and IT departments ban IP addresses or ban popular third-party services
A better option would be to use a honey pot or wait for human behaviour such as a click.
Better Security With Privacy Without Annoying Users:
- Two or Three-Step login process where the user clicks something to bring up a generated login form.
- The user clicks a button to bring up the password form separately from the username.
- The user clicks can act as a CAPTCHA method using a honey pot such as a hidden check-box or another input form.
- The contact us form of both Ojambo.com and OjamboServices.com implement a tweaked hidden honey pot and never receive spam.
- No tracking on the login screen to prevent hackers from stealing credentials.
Sites that really care about user security should not compromise on privacy. Two-Factor Authentication should not be though of as a secure method because it utilizes two of the most insecure methods of communication. Email, phone voice call and phone text message are not secure as they are unencrypted methods of communication.
References
🚀 Recommended Resources
Disclosure: Some of the links above are referral links. I may earn a commission if you make a purchase at no extra cost to you.